Misc
签到
观察了一下,发现是unicode编码
def decode_unicode(dec_list):
decoded_chars = []
for dec in dec_list:
decoded_chars.append(chr(dec))
return ''.join(decoded_chars)
unicode_decimals = [
27880, 30693, 25915, 21892, 38450, 23454, 39564, 23460, 21457, 36865,
112, 108, 98, 99, 116, 102, 33719, 21462, 21069, 27573, 102, 108, 97,
103, 20851, 27880, 79, 110, 101, 45, 70, 111, 120, 23433, 20840, 22242,
38431, 22238, 22797, 112, 108, 98, 99, 116, 102, 33719, 21462, 21518,
27573, 102, 108, 97, 103
]
decoded_text = decode_unicode(unicode_decimals)
print(decoded_text)
#注知攻善防实验室发送plbctf获取前段flag关注One-Fox安全团队回复plbctf获取后段flagflag{TreJaiuLT1rgbdfG0Eay}
江

提交格式: flag{xx省xx市xxx路与xx路xx街交叉路口}
逆天,我去过这里,,一眼江汉路我曹,属实难绷,注意到旁边有个新金珠宝,然后谷歌地图一搜

flag{湖北省武汉市江汉二路与江汉路步行街交叉路口}
fm145.8
老题了,rxsstv梭了
什么协议?
随便翻翻在http/json协议中找到了个假flag,盲猜真flag也在http/json协议,过滤网络流


一眼看出flag
然后百度发现是块排序压缩BWT解码: flag{go0d_finder_f0r_th1s}
Reverse
Login_System

进入验证成功的函数

易得加密逻辑
简单xor
写解密脚本
A=[0x2A, 0x2A, 0x55, 0x55, 0x2A, 0x55, 0x2A, 0x2A, 0x2A, 0x2A, 0x2A, 0x2A, 0x2A, 0x2A, 0x2A, 0x2A, 0x2A, 0x2A, 0x2A, 0x2A, 0x2A, 0x55, 0x55, 0x2A, 0x2A, 0x55, 0x2A, 0x2A, 0x2A, 0x2A, 0x55, 0x55, 0x55, 0x55, 0x2A, 0x2A, 0x2A, 0x55, 0x55, 0x55, 0x55, 0x2A, 0x55, 0x55, 0x55, 0x2A, 0x55, 0x55, 0x55, 0x2A, 0x2A, 0x2A, 0x2A, 0x2A, 0x2A, 0x2A, 0x2A, 0x55, 0x2A, 0x2A, 0x2A, 0x2A, 0x55, 0x55, 0x55, 0x55, 0x2A, 0x55, 0x55, 0x55, 0x55, 0x55, 0x2A, 0x2A, 0x2A, 0x55, 0x55, 0x55, 0x2A, 0x55, 0x55, 0x55, 0x55, 0x2A, 0x2A, 0x2A, 0x2A, 0x2A, 0x55, 0x55, 0x55, 0x55, 0x55, 0x2A, 0x55, 0x2A, 0x2A, 0x2A, 0x55, 0x2A, 0x55, 0x2A, 0x2A, 0x2A, 0x55, 0x55, 0x55, 0x2A, 0x2A, 0x2A, 0x00]
for i in range(len(A)):
A[i]=chr(A[i]^0xA)
print(A[i], end='')
B=[0x2B, 0x24, 0x2B, 0x54, 0x77, 0x2B, 0x77, 0x2B, 0x54, 0x54, 0x2B, 0x54, 0x2B, 0x2B, 0x54, 0x54, 0x2B, 0x54, 0x2B, 0x2B, 0x24, 0x2B, 0x24, 0x2B, 0x24, 0x2B, 0x57, 0x2B, 0x2B, 0x24, 0x2B, 0x54, 0x54, 0x54, 0x77, 0x2B, 0x24, 0x2B, 0x54, 0x54, 0x54, 0x77, 0x54, 0x2B, 0x54, 0x77, 0x54, 0x2B, 0x54, 0x77, 0x2B, 0x2B, 0x2B, 0x2B, 0x2B, 0x2B, 0x24, 0x2B, 0x57, 0x2B, 0x2B, 0x77, 0x2B, 0x2B, 0x54, 0x2B, 0x57, 0x54, 0x2B, 0x2B, 0x2B, 0x54, 0x77, 0x2B, 0x77, 0x54, 0x2B, 0x54, 0x24, 0x2B, 0x54, 0x54, 0x54, 0x77, 0x2B, 0x2B, 0x2B, 0x77, 0x2B, 0x2B, 0x54, 0x54, 0x54, 0x77, 0x2B, 0x77, 0x2B, 0x77, 0x2B, 0x77, 0x2B, 0x57, 0x2B, 0x77, 0x2B, 0x57, 0x2B, 0x57, 0x2B, 0x2B, 0x00]
for i in range(len(B)):
B[i]=chr(B[i]^0xB)
print(B[i], end='')
C=[0x70, 0x2C, 0x70, 0x53, 0x70, 0x2C, 0x70, 0x23, 0x2C, 0x53, 0x6C, 0x2C, 0x70, 0x23, 0x2C, 0x53, 0x6C, 0x2C, 0x70, 0x70, 0x2C, 0x70, 0x2C, 0x23, 0x2C, 0x53, 0x2C, 0x50, 0x2C, 0x50, 0x53, 0x53, 0x53, 0x2C, 0x50, 0x70, 0x2C, 0x70, 0x2C, 0x2C, 0x2C, 0x2C, 0x70, 0x2C, 0x70, 0x2C, 0x70, 0x2C, 0x70, 0x2C, 0x2C, 0x2C, 0x2C, 0x2C, 0x2C, 0x23, 0x2C, 0x53, 0x2C, 0x50, 0x2C, 0x70, 0x2C, 0x70, 0x53, 0x25, 0x2C, 0x70, 0x70, 0x2C, 0x70, 0x2C, 0x2C, 0x2C, 0x2C, 0x70, 0x2C, 0x70, 0x50, 0x53, 0x53, 0x53, 0x2C, 0x50, 0x2C, 0x2C, 0x2C, 0x70, 0x2C, 0x70, 0x53, 0x2C, 0x2C, 0x70, 0x2C, 0x70, 0x2C, 0x70, 0x2C, 0x70, 0x2C, 0x2C, 0x50, 0x70, 0x2C, 0x70, 0x70, 0x2C, 0x70, 0x2C, 0x00]
for i in range(len(C)):
C[i]=chr(C[i]^0xC)
print(C[i], end='')
D=[0x71, 0x2D, 0x2D, 0x52, 0x71, 0x2D, 0x71, 0x2D, 0x25, 0x52, 0x71, 0x2D, 0x71, 0x2D, 0x25, 0x52, 0x71, 0x2D, 0x31, 0x2D, 0x31, 0x2D, 0x22, 0x2D, 0x52, 0x52, 0x52, 0x2D, 0x51, 0x2D, 0x52, 0x52, 0x52, 0x24, 0x2D, 0x71, 0x2D, 0x71, 0x52, 0x52, 0x52, 0x2D, 0x71, 0x2D, 0x71, 0x2D, 0x71, 0x2D, 0x71, 0x2D, 0x2D, 0x2D, 0x2D, 0x2D, 0x22, 0x2D, 0x52, 0x52, 0x52, 0x2D, 0x51, 0x71, 0x2D, 0x2D, 0x52, 0x2D, 0x31, 0x2D, 0x71, 0x2D, 0x71, 0x2D, 0x2D, 0x2D, 0x2D, 0x71, 0x2D, 0x71, 0x2D, 0x52, 0x52, 0x52, 0x24, 0x2D, 0x71, 0x2D, 0x2D, 0x71, 0x2D, 0x2D, 0x52, 0x71, 0x2D, 0x71, 0x2D, 0x71, 0x52, 0x71, 0x2D, 0x71, 0x2D, 0x71, 0x51, 0x2D, 0x2D, 0x71, 0x2D, 0x33, 0x2D, 0x33, 0x00]
for i in range(len(D)):
D[i]=chr(D[i]^0xD)
print(D[i], end='')
E=[0x72, 0x51, 0x72, 0x2E, 0x72, 0x51, 0x72, 0x52, 0x51, 0x51, 0x22, 0x51, 0x72, 0x52, 0x51, 0x51, 0x22, 0x2E, 0x72, 0x72, 0x2E, 0x21, 0x51, 0x21, 0x2E, 0x2E, 0x2E, 0x52, 0x51, 0x52, 0x51, 0x51, 0x51, 0x51, 0x21, 0x2E, 0x52, 0x51, 0x51, 0x51, 0x51, 0x72, 0x51, 0x51, 0x51, 0x72, 0x51, 0x51, 0x51, 0x72, 0x51, 0x51, 0x51, 0x21, 0x51, 0x21, 0x2E, 0x2E, 0x2E, 0x52, 0x51, 0x52, 0x51, 0x72, 0x2E, 0x52, 0x51, 0x52, 0x72, 0x51, 0x72, 0x51, 0x51, 0x51, 0x72, 0x51, 0x51, 0x51, 0x72, 0x51, 0x51, 0x51, 0x51, 0x21, 0x51, 0x51, 0x51, 0x72, 0x51, 0x72, 0x2E, 0x2E, 0x2E, 0x2E, 0x52, 0x51, 0x51, 0x51, 0x21, 0x72, 0x51, 0x72, 0x2E, 0x52, 0x51, 0x72, 0x72, 0x2E, 0x72, 0x2E, 0x00]
for i in range(len(E)):
E[i]=chr(E[i]^0xE)
print(E[i], end='')
F=[0x2F, 0x2F, 0x2F, 0x2F, 0x2F, 0x2F, 0x2F, 0x2F, 0x2F, 0x2F, 0x2F, 0x2F, 0x2F, 0x73, 0x50, 0x50, 0x50, 0x20, 0x2F, 0x2F, 0x53, 0x50, 0x53, 0x2F, 0x2F, 0x2F, 0x2F, 0x2F, 0x2F, 0x2F, 0x2F, 0x2F, 0x2F, 0x2F, 0x2F, 0x2F, 0x2F, 0x2F, 0x2F, 0x2F, 0x2F, 0x2F, 0x2F, 0x2F, 0x2F, 0x2F, 0x2F, 0x2F, 0x73, 0x50, 0x50, 0x50, 0x50, 0x50, 0x73, 0x2F, 0x2F, 0x2F, 0x2F, 0x2F, 0x2F, 0x2F, 0x2F, 0x2F, 0x2F, 0x2F, 0x2F, 0x2F, 0x2F, 0x73, 0x50, 0x50, 0x50, 0x50, 0x50, 0x73, 0x2F, 0x2F, 0x2F, 0x2F, 0x2F, 0x2F, 0x73, 0x50, 0x50, 0x50, 0x50, 0x50, 0x73, 0x2F, 0x2F, 0x2F, 0x2F, 0x2F, 0x2F, 0x2F, 0x2F, 0x2F, 0x2F, 0x2F, 0x2F, 0x2F, 0x2F, 0x2F, 0x2F, 0x20, 0x50, 0x20, 0x2F, 0x2F, 0x00]
for i in range(len(F)):
F[i]=chr(F[i]^0xF)
print(F[i], end='')
PyLu
pyins解包+pycdc反编译
from Crypto.Util.number import bytes_to_long
def enc(key):
R = bytes_to_long(b'Welcome To PaluCTF!')
MOD = 2 ** 418
R = R ^ R - 60 >> 24
R = R ^ R - 60 << 88
R ^= key
R = -R ** 2 * 2024 % MOD
R = R * key % MOD
return R
flag = input('Welcome To PaluCTF!\nInput FLAG:')
m = bytes_to_long(flag.encode())
cor = 0x2E441F765514CCA89173554726494D37E9FBE774B6F807BC5F6E71117530CE3D7DB5F70554C03CD9055F4E42969600904DF1F4DB8L
if enc(m) == cor:
print('Congratulation!')
return None
print('Wrong FLAG!')不会解
赛后看了一下,竟然能用z3解
import z3
from Crypto.Util.number import *
def enc(key):
R = bytes_to_long(b"Welcome To PaluCTF!")
MOD = 2**418
R = R ^ ((R - 60) >> 24)
R = R ^ ((R - 60) << 88)
R ^= key
R = (-R * R * 2024) % MOD
R = (R * key) % MOD
return R
res = 0x2E441F765514CCA89173554726494D37E9FBE774B6F807BC5F6E71117530CE3D7DB5F70554C03CD9055F4E42969600904DF1F4DB8
s = z3.Solver()
key = z3.BitVec("key", 418)
s.add(enc(key) == res)
s.check()
m = s.model()
flag = long_to_bytes(m[key].as_long())
print(flag)
# b'flag{e88f88d7-4d75-462b-8447-bf4ab7aeab1a}'Z3一把梭:用约束求解搞定一类CTF题 - 知乎 (zhihu.com)
看了这篇文章感觉还是有收获的,这道题的enc函数全是一系列的位操作,利用bitVec进行z3约束求解是比较符合的,以下为赛后复现
ezre签到
刚开始看这道题就Go语言给吓到了就没看了,其实这道题的逻辑也不复杂

就是从本地os中读入local.txt的内容,然后进行一个加密,然后保存到本地的encrypt.txt的文件当中
整个代码的流程:
-
首先,这段代码读取了一个名为"local.txt"的文件
-
然后,它创建了一个映射(map),并将一些字符映射到了不同的整数值。这可能是一个字符替换的加密方法 runtime_makemap
-
接下来,它遍历了输入文件的每个字符,使用上面创建的映射进行替换:
-
最后,它将加密后的内容写入到一个名为"encrypted.txt"的文件中
看了别的队的wp,是利用在local.txt中写入abcdefghijklmnopqrstuvwxyz 然后获得加密文本进行逆向替换的, 如果加密算法是块类型的话或者更复杂一点的而不是单表替换 显然就无法奏效了
还是要把解密算法给逆清楚,但是go语言的函数一堆接口,以及数据结构看起来有点吃力
最近太忙了,还是先挖着坑吧
Go二进制文件逆向分析从基础到进阶——综述-安全客 - 安全资讯平台 (anquanke.com)
帕鲁被病毒感染了
题目说明:电脑中的重要文件被APT组织的勒索病毒s感染,请从受感染的文件中获取标记病毒样本
附件给了一个压缩包和一个图片,有明显的切割痕迹,盲猜宽高有问题,用CRC脚本计算了一下宽高
可以得到压缩包密码palubei@2024#01

先看看最近修改的地方:manifest.json和repositories,manifest是配置文件,跳过不看
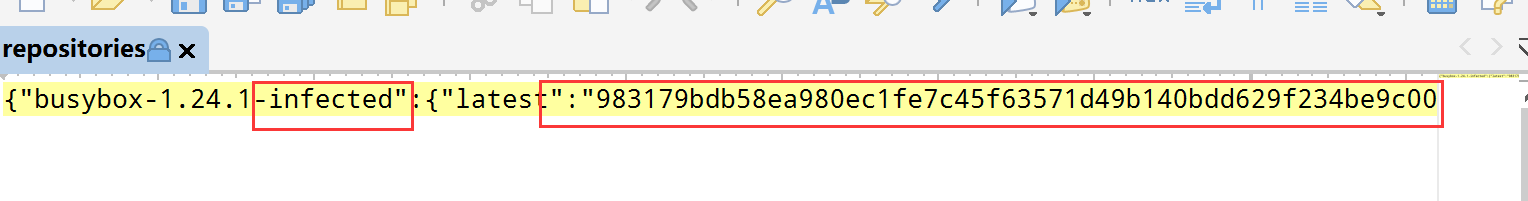
可知983开头的文件受到了病毒感染
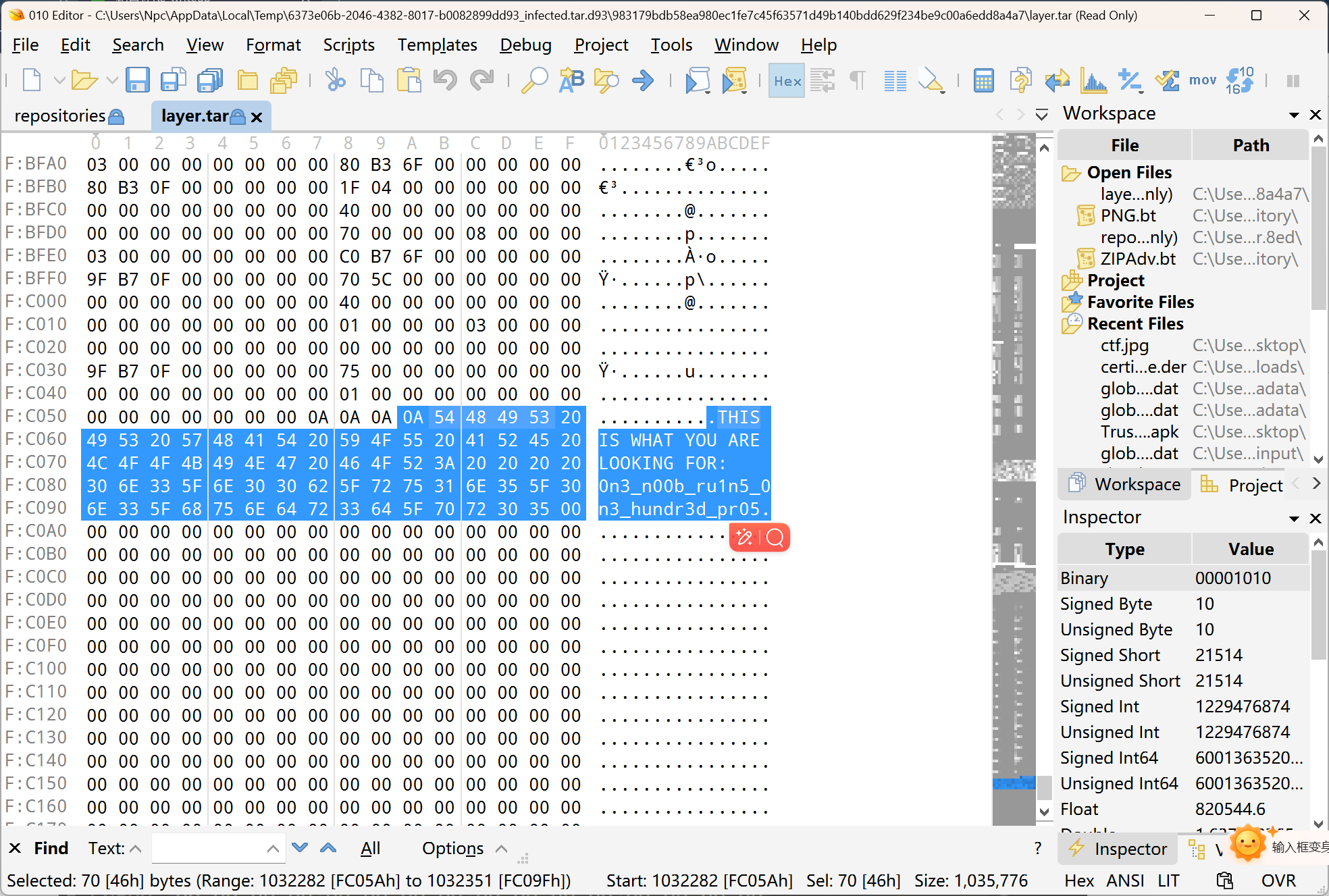
然后在文件尾部发现了flag
o2

查不出壳,应该是结构损坏
用ida打开提示The ELF header entry size is invalid (16944,expected 52
并且ida认为该文件为64位程序
盲猜把headers修改成32位程序了
ELF文件解析(二):ELF header详解 - JollyWing - 博客园 (cnblogs.com)
那就改第4位为2 , 修改后程序就可以用ida反编译了
交叉引用input:
这个是initarray函数,程序初始化后会赋值

继续跟踪input,进入加密函数

""" #正向逻辑
a2='PaluCTF'
a1='???'
enc=''
for i in range(len(a1)):
enc+=(chr(ord(a1)+ord(a2[i%len(a2)]))%128
# enc = bytearray.fromhex("364d4d5c3e387e00421c597a0a7302144d5b70087e064619567336297d151f56770a7935424f2a780643")
"""
#用爆破的方法
from string import printable
enc=bytearray.fromhex("364d4d5c3e387e00421c597a0a7302144d5b70087e064619567336297d151f56770a7935424f2a780643")
a2='PaluCTF'
flag=''
for i in range(len(enc)):
for j in printable:
if (ord(j)+ord(a2[i%len(a2)]))%128==enc[i]:
flag+=j
break
print(flag)茶
赛后看wp得知是chacha20加密
【密码学】一文读懂ChaCha20-阿里云开发者社区 (aliyun.com)

这是ChaCha20 1/4轮运算 ,根据这个也许能识别该算法

然而直接解发现不对(我对这个算法还没研究明白)

其中,KEY_INIT由 4部分组成:
KEY_INIT[0]~ KEY_INIT[15]是 16字节的常量(constant);
KEY_INIT[16]~ KEY_INIT[47]是 32字节的 key;
KEY_INIT[48]~ KEY_INIT[51]是 4字节的 block counter;
KEY_INIT[52]~ KEY_INIT[63]是 12字节的 nonce。v28显然是key矩阵 ,然而发现key_init过程只用到了v7即nonce的前8位,所以应该截取字节前8位??
Crypto
签到
ncat 127.0.0.1 49864
Hi Palu
c: 98876521470072624847831191120242836106634355424904228449087001789377274256416817164244577293275751367364395746152926908677673395240842983543626309956125791650694384718948488185393751748362820849920814315154022729348607056257917664879714097211171557337934164726557707762046162288673723358830278187038021933
p: 7634191592858328303720104201829885550642551766588082120933566851869152621875807377947599043353915886710003110588252519891078329707680245639560965044434287
e: 65537
n: 58280881276468779903608011114914198014673498168050506689306037336115277380066112347231925972016586673995546398141197761523506547955670113470312322471449026567491240807076753530685478376076520013004565837697497794992610136881131655961111391642576499716138406614344634751082699734458229688725947588315861198369注意这题有点坑,n,p,q比较大,导致python运算会精度丢失,不能用python算,这里我用了sage计算了m
sage: p
7634191592858328303720104201829885550642551766588082120933566851869152621875807377947599043353915886710003110588252519891078329707680245639560965044434287
sage: c
98876521470072624847831191120242836106634355424904228449087001789377274256416817164244577293275751367364395746152926908677673395240842983543626309956125791650694384718948488185393751748362820849920814315154022729348607056257917664879714097211171557337934164726557707762046162288673723358830278187038021933
sage: phi=euler_phi(p*p)
sage: phi
58280881276468779903608011114914198014673498168050506689306037336115277380066112347231925972016586673995546398141197761523506547955670113470312322471449018933299647948748449810581276546190969370452799249615376861425758267728509780153733444043533145800251696611234046498562808656128522008480308027350816764082
sage: d=inverse_mod(65537,phi)
sage: m=pow(c,d,n)
sage: m
56006392793429523037794282557491225182378548607499316967118649585021715585142102903175863079701722493
#b'flag{ef517c5e-0a09-4900-a2b0-b26e500e4f65}'玛卡巴卡
玛卡巴卡玛卡巴卡轰达姆阿卡嗙轰阿巴雅卡阿巴雅卡阿巴雅卡轰达姆阿卡嗙轰哈姆达姆阿卡嗙哈姆达姆阿卡嗙哈姆达姆阿卡嗙轰玛卡巴卡轰达姆阿卡嗙轰阿巴雅卡阿巴雅卡轰咿呀呦轰达姆阿卡嗙轰一般这种都是16进制替换感觉
好吧,是玛卡巴卡编码,很难绷,这种题感觉没什么意义,我当时搜好久玛卡巴卡编码没搜到
def decode_text(encoded_text, encoding_rules):
decoded_text = ''
i = 0
while i < len(encoded_text):
found = False
for letter, code in encoding_rules.items():
if encoded_text[i:i+len(code)] == code:
decoded_text += letter
i += len(code)
found = True
break
if not found:
# 如果无法解码,则保留原编码
decoded_text += encoded_text[i]
i += 1
return decoded_text
# 编码字典
encoding_rules = {
'a': '玛卡巴卡轰', 'b': '阿巴雅卡轰','c': '伊卡阿卡噢轰', 'd':'哈姆达姆阿卡嗙轰','e': '咿呀呦轰','f': '玛卡雅卡轰','g': '伊卡阿卡轰','h': '咿呀巴卡轰','i': '达姆阿卡嗙轰','j': '玛卡巴卡玛卡巴卡轰','k': '玛卡巴卡玛卡巴卡玛卡巴卡轰','l': '玛卡巴卡玛卡巴卡玛卡巴卡玛卡巴卡轰','m': '阿巴雅卡阿巴雅卡轰','n': '阿巴雅卡阿巴雅卡阿巴雅卡轰','o': '阿巴雅卡阿巴雅卡阿巴雅卡阿巴雅卡轰','p': '伊卡阿卡噢伊卡阿卡噢轰','q': '伊卡阿卡噢伊卡阿卡噢伊卡阿卡噢轰','r': '伊卡阿卡噢伊卡阿卡噢伊卡阿卡噢伊卡阿卡噢轰','s': '哈姆达姆阿卡嗙哈姆达姆阿卡嗙轰','t': '哈姆达姆阿卡嗙哈姆达姆阿卡嗙哈姆达姆阿卡嗙轰','u': '哈姆达姆阿卡嗙哈姆达姆阿卡嗙哈姆达姆阿卡嗙哈姆达姆阿卡嗙轰','v': '咿呀呦咿呀呦轰','w': '咿呀呦咿呀呦咿呀呦轰','x': '咿呀呦咿呀呦咿呀呦咿呀呦轰','y': '咿呀呦咿呀呦咿呀呦咿呀呦咿呀呦轰','z': '玛卡雅卡玛卡雅卡轰','A': '玛卡雅卡玛卡雅卡玛卡雅卡轰','B': '玛卡雅卡玛卡雅卡玛卡雅卡玛卡雅卡轰','C': '伊卡阿卡伊卡阿卡轰','D': '伊卡阿卡伊卡阿卡伊卡阿卡轰','E': '伊卡阿卡伊卡阿卡伊卡阿卡伊卡阿卡轰','F': '咿呀巴卡咿呀巴卡轰','G': '咿呀巴卡咿呀巴卡咿呀巴卡轰','H': '咿呀巴卡咿呀巴卡咿呀巴卡咿呀巴卡轰','I': '咿呀巴卡咿呀巴卡咿呀巴卡咿呀巴卡咿呀巴卡轰','J': '达姆阿卡嗙达姆阿卡嗙轰','K': '达姆阿卡嗙达姆阿卡嗙达姆阿卡嗙轰','L': '达姆阿卡嗙达姆阿卡嗙达姆阿卡嗙达姆阿卡嗙轰','M': '达姆阿卡嗙达姆阿卡嗙达姆阿卡嗙达姆阿卡嗙达姆阿卡嗙轰','N': '巴卡巴卡轰','O': '巴卡巴卡巴卡巴卡轰','P': '巴卡巴卡巴卡巴卡巴卡巴卡轰','Q': '巴卡巴卡巴卡巴卡巴卡巴卡巴卡巴卡轰','R': '巴卡巴卡巴卡巴卡巴卡巴卡巴卡巴卡巴卡巴卡轰','S': '呀呦轰','T': '呀呦呀呦轰','U': '呀呦呀呦呀呦轰','V': '呀呦呀呦呀呦呀呦轰','W': '呀呦呀呦呀呦呀呦呀呦轰','X': '达姆阿卡轰','Y': '达姆阿卡达姆阿卡轰','Z': '达姆阿卡达姆阿卡达姆阿卡轰','0': '达姆阿卡达姆阿卡达姆阿卡达姆阿卡轰','1': '达姆阿卡达姆阿卡达姆阿卡达姆阿卡达姆阿卡轰','2': '玛巴轰','3': '玛巴玛巴轰','4': '玛巴玛巴玛巴轰','5': '玛巴玛巴玛巴玛巴轰','6': '巴卡玛巴轰','7': '巴卡玛巴巴卡玛巴轰','8': '巴卡玛巴巴卡玛巴巴卡玛巴轰','9': '巴卡玛巴巴卡玛巴巴卡玛巴巴卡玛巴轰','=': '妈个巴子轰','/': '妈个巴卡轰','+': '妈个巴达轰',
}
# 要解码的编码消息
encoded_message = "玛卡巴卡玛卡巴卡轰达姆阿卡嗙轰阿巴雅卡阿巴雅卡阿巴雅卡轰达姆阿卡嗙轰哈姆达姆阿卡嗙哈姆达姆阿卡嗙哈姆达姆阿卡嗙轰玛卡巴卡轰达姆阿卡嗙轰阿巴雅卡阿巴雅卡轰咿呀呦轰达姆阿卡嗙轰"
# 解码消息
decoded_message = decode_text(encoded_message, encoding_rules)
print(decoded_message)Web
签到
from flask import Flask, request, jsonify
import requests
flag='123' # 假设从 flag.py 文件中导入了 flag 函数
app = Flask(__name__)
@app.route('/', methods=['GET', 'POST'])
def getinfo():
url = request.args.get('url')
print("This is url",url)
if url:
# 请求url
response = requests.get(url)
content = response.text
print(content)
if "paluctf" in content:
return flag
else:
return content
else:
response = {
'message': 200, # 这里是数值,不是字符串
'data': "Come sign in and get the flag!"
}
return jsonify(response)
@app.route('/flag', methods=['GET', 'POST'])
def flag1():
return "paluctf"
if __name__ == '__main__':
app.run(debug=True, host="0.0.0.0", port=80)payload:
http://127.0.0.1:36914/?url=http://127.0.0.1/flagflag{baca6a54-66d7-4786-951b-78acafa4cf91}
应急响应
1
